In today’s Geek School lesson, we’re going to explain how to use the Local Group Policy editor to make changes to your PC that aren’t available any other way.
We should note right up-front that the Group Policy editor is only available in the Pro versions of Windows – Home or Home Premium users won’t have access to it. It’s still worth learning about though.
Group Policies are a really powerful way to setup a corporate network with each of the computers locked down so users can’t mess them up with unwanted changes, and stop them from running unapproved software, among many other uses.
In the home environment, however, you probably won’t want to set password length restrictions or force yourself to change your password. And you probably won’t need to lock down your machines to only run specific approved executables.
There are many other things that you can configure though, like disabling Windows features that you don’t like, blocking certain applications from running, or creating scripts that run during Logon or Logoff.
Understanding the Interface
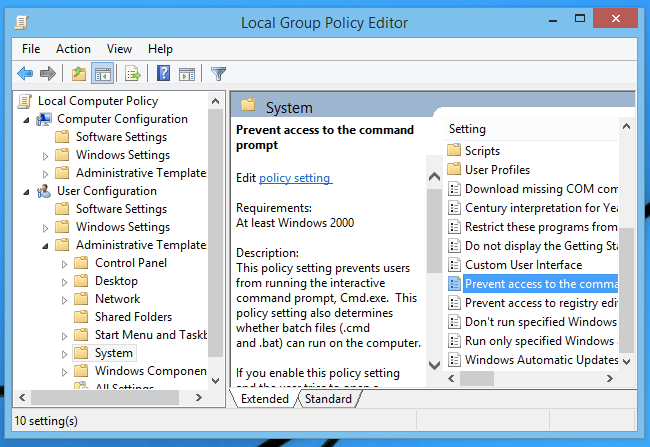
The interface is very similar to every other administration tool – the treeview on the left allows you to look for settings in a hierarchical folder structure, there is a list of settings, and a preview panel that gives you more information about the particular setting.
There are two top-level folders to be aware of:
- Computer Configuration – holds settings that are applied to computers regardless of which user is logging in.
- User Configuration – holds settings that are applied to user accounts.
Under each of these folders there are a couple of folders that allow you to drill down further into the available settings:
- Software Settings – this folder is meant for software-related configurations and is blank by default on client Windows.
- Windows Settings – this folder holds security settings and scripts for logon/logoff and startup/shutdown.
- Administrative Templates – this folder holds registry-based configurations, which are essentially a quick way to tweak settings on your computer or for your user account. There are a lot of available settings.
Tweaking Security Rules
If you were to double-click on the “Prevent access to the command prompt” item from the screenshot above, you would be presented with a window that looks like this one – in fact, most of the settings under Administrative Templates are going to look similar.
This particular setting would allow you to block access to the command prompt for users on the PC. You can also configure the setting inside the dialog to block batch files as well.

Another option in the same folder allows you to create a setting for “Run only specified Windows applications” – you would configure the setting to Enabled and then provide a list of allowed applications. Everything else would be blocked from running.

In this case, if you were to run an application that isn’t on the list, you would get an error message like this one.

It’s worth noting that messing with rules like this could lock you out of your PC if you do something wrong, so be careful.
Tweaking UAC Settings for Security

Under the Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options folder, you’ll find a bunch of interesting settings to make your computer a bit more secure.
The first option can be found in that folder as the item “User Account Control: Behavior of the elevation prompt for Administrators”, and if you choose “Prompt for credentials on the secure desktop”, it will force you (or another user) to enter your password anytime you try to run something in administrator mode.
This option makes Windows work more like Linux or Mac, where you are asked to provide your password any time you need to make a change, and since the Secure Desktop doesn’t allow any other applications to mess with the dialog, it’s a lot more secure.

Other useful options:
- User Account Control: Only elevate executables that are signed and validated – this option prohibits applications that aren’t digitally signed from running as administrator.
- Recovery console, allow automatic administrative logon – when you need to use the recovery console to perform system tasks, you generally have to provide the administrator password. If you happened to forget that password, this would allow you to get in to reset it more easily. (And since you can easily wipe a Windows password, it isn’t really less secure).
One thing that’s worth noting is that many of the policies in the list don’t actually apply to every Windows version. For example, in the screenshot below, the “Remove My Documents Icon” setting is only available for Windows XP and 2000. Certain other policies will say “At least Windows XP” or something like that, which would mean they will continue to work on all versions.

There are an enormous number of settings in the Group Policy editor, so it is definitely worth spending some time looking through them if you’re curious. Most of the settings allow you to disable Windows features that you don’t particularly like – very few give you functionality that you didn’t have by default.
Setting Up Scripts to Run at Logon, Logoff, Startup, or Shutdown

Yet another example of something you can only do using the Group Policy editor is setting up a logoff or shutdown script to run every time you reboot your PC.
This can be really useful for cleaning up your system or making a quick backup of certain files every time you shut down, and you can use batch files or even PowerShell scripts for either. The only caveat is that these scripts must run silently or they will lock up the logoff process.
There are two different types of scripts that you can run.
- Startup / Shutdown Scripts – these scripts are found under Computer Configuration -> Windows Settings -> Scripts and will be run under the Local System account, so they can manipulate system files, but won’t be running as your user account.
- Logon / Logoff Scripts – these scripts are found under User Configuration -> Windows Settings -> Scripts and will be run under your user account.
It’s worth noting that the logon and logoff scripts won’t let you run utilities that require administrator access unless you’ve got UAC completely disabled.
For today’s example, we’ll make a logoff script by heading down to User Configuration -> Windows Settings -> Scripts and double-clicking on Logoff.

The Logoff properties window allows you to add multiple logoff scripts to run.

You can also configure PowerShell scripts instead.

The really important thing to note here is that your scripts need to be in a particular folder for them to work properly.
Logon and Logoff Scripts will need to be in the following folders:
- C:\Windows\System32\GroupPolicy\User\Scripts\Logoff
- C:\Windows\System32\GroupPolicy\User\Scripts\Logon
While Startup and Shutdown Scripts will need to be in these folders:
- C:\Windows\System32\GroupPolicy\Machine\Scripts\Shutdown
- C:\Windows\System32\GroupPolicy\Machine\Scripts\Startup
Once you’ve configured your logoff script, you can test it out – we setup a simple script that created a text file on the desktop, and then logged off and back on. But you could make it do anything you wanted.

And of course, if you were doing a logon script instead, it could actually launch applications.
One important thing to note is that if your script prompts for user input, Windows will hang during shutdown or logoff for 10 minutes before the script is killed and Windows can reboot. This is something you should definitely keep in mind when designing your script.
Group Policy Doesn’t End Here
We just scratched the surface for what Group Policy can really do, and in a corporate domain environment it is one of the most powerful and important tools at your disposal. Since this series isn’t about IT users, we won’t go into all of the rest, but it’s worthwhile to do some research on your own.








No comments:
Post a Comment